To make it easier for people in charge of “STIG’ing” their SQL Server 2016 environment, this blog is aimed to go over the newest MS SQL Server 2016 STIG Overview document (Version 1, Release 1) that was released on 09 March 2018. If you want to read through the whole document you can download it here. Otherwise, below is my summation of the relevant sections.
This overview document was developed by both Microsoft and DISA for the Department of Defense.
The entire overview document is 9 pages (including title page, etc.)

INTRODUCTION
Section 1.1 – Executive Summary
It just states the basic information that the MS SQL Server 2016 STIG is published as two documents. One for the database, and one for the instance.
Section 1.2 – Authority
This section describes what DoD Instruction (DoDI) 8500.01 requires. It pretty much says that all IT that receives/transmits/stores/displays DoD information will have to be configured in accordance to DoD cyber security policies. You can read the entire 59 page document here, or just skip to page 4 and read section “h.(1) Information Technology”
Note: This document is only for DoDI 8500.01. IF your systems security requirements need to meet NIST SP 800-53, you will have to look up CNSSI 1253. Or just click here :)
Section 1.3 – Vulnerability Severity Category Code Definitions
Severity Category Code (referred to as CAT) measure the severity in which a vulnerability can cause harm and needs to be remedied. Each vulnerability is given one of the following based on severity, CAT I, CAT II, CAT III.
Below is a snapshot of what each one means:
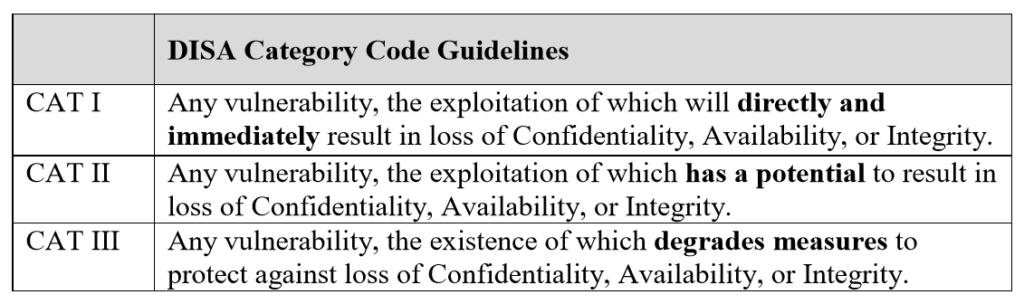
Section 1.4 – STIG Distribution
All latest copies of STIG can be found on the Information Assurance Support Environment (IASE) website here.
Section 1.7 – Other Considerations
This is just the “CYA” portion of the document. “DISA accepts no liability for the consequences…” etc. etc.
Section 1.8 – Product Approval Disclaimer
This is important to note; Just because you have a STIG does not mean you have DoD approval for the use of the product. The STIGs just provide security guidance for products being used by the DoD. In addition to the environment being STIG’d, it is important to have proper security documentation. A DoD Authorizing Official (AOs) may ask for this information.
ASSESSMENT CONSIDERATIONS
Section 2.1 – Security Assessment Information
Just a warning that this document is only one aspect of the entire defense-in-depth solution. The SQL Server 2016 STIG will only be successful if the Windows and Network STIGs are also applied.
This does not provide a procedure, as to how to STIG an SQL Server?
Hey Michael, I have not had the chance to get around to posting SQL Server 2016 STIGs (like I have for 2012). Hopefully in the near future I will. If you have any specific questions in the meantime, feel free to contact me and I’ll try to help!
Michael, if you are looking for some automation, check out ASSET (Automated SQL Security Evaluation Tool) at Borelli Security Software. It can scan and evaluate SQL Server and produce the latest DISA checklists for both SQL Server 2014 & 2016.
Mohammad has had a look at it (though I don’t know if he’s seen the 2014 suite, yet) and maybe he can tell you what he thinks (since I am obviously biased).
hi mohammad,
could you please provide the xerox copu of Exam Ref [70-764] Administering a SQL Database Infrastructure book and practice questions
brahmareddysqldba@gmail.com